Kerberos authentication ~ Kerberos is used to protect services and uses a ticket-based authentication protocol to authenticate users. Using Kerberos authentication within a domain or in a forest allows the user or service access. Indeed recently has been hunted by consumers around us, maybe one of you personally. People are now accustomed to using the internet in gadgets to see video and image information for inspiration, and according to the title of the post I will discuss about Kerberos Authentication Passwords are never sent across the network because only keys are sent in an encrypted form.
If you re looking for Kerberos Authentication you've reached the perfect place. We have 6 graphics about kerberos authentication including pictures, photos, photographs, wallpapers, and more. In such web page, we also have variety of images available. Such as png, jpg, animated gifs, pic art, symbol, blackandwhite, translucent, etc.

Kerberos Authentication Architecture Ile Ilgili Gorsel Sonucu Cryptography Architecture Kas
Source Image @ tr.pinterest.com
When the file server gets the token it decrypts not encrypts the token with the secret key shared with TGS.

Kerberos authentication. You can configure Elasticsearch to use the Kerberos V5 authentication protocol which is an industry standard protocol to authenticate users. In Kerberos Authentication server and database is used for client authentication. Kerberos Authentication requires some specific configuration on the Active Directory server and Oracle VDI hosts prior to setting up the user directory in the Oracle VDI Manager.
This allows for strong and secure authentication. Kerberos is an authentication protocol for clientserver applications. The Windows Server operating systems implement the Kerberos version 5 authentication protocol and extensions for public key and password-based authentication.
The next step includes the registration of Service Principal Name SPN entries for the name of the website which will be accessed by the users. In this tutorial we are going to show you how to authenticate Nginx users using the Active Directory from Microsoft Windows and the Kerberos protocol. Negotiate is a container that uses Kerberos as the first authentication method and if the authentication fails NTLM is used.
In our example the domain controller IP address is 1921681510. Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux. Kerberos is available in many commercial products as well.
Kerberos ˈkɜːrbərɒs is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to. The principal advantages in adopting Kerberos as an authentication service are. The Kerberos authentication client is implemented as a security support provider SSP which can be accessed through the Security Support Provider Interface SSPI.
Basically Kerberos is a network authentication protocol that works by using secret key cryptography. The Oracle Kerberos authentication adapter utilities are designed for an Oracle client with Oracle Kerberos authentication support installed. Kerberos is a network authentication protocol.
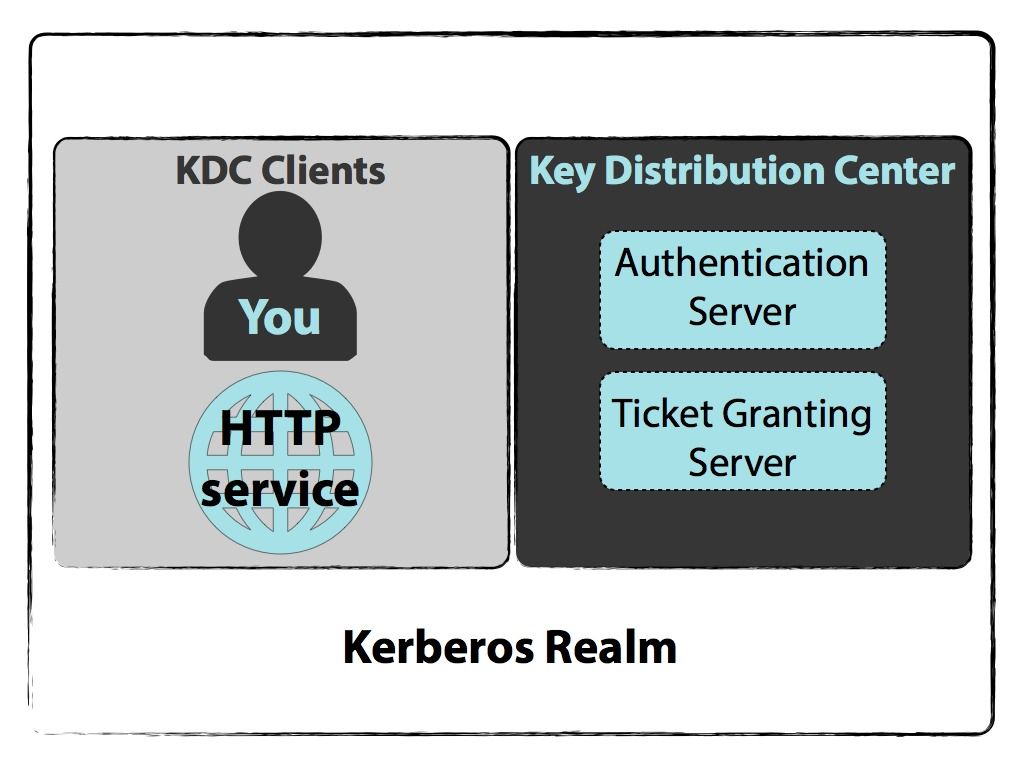
In our world Kerberos is the computer network authentication protocol initially developed in the 1980s by Massachusetts Institute of Technology MIT computer scientists. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC. Read on to learn what Kerberos authentication is and how it protects both end-users and systems.
Clients authenticate with a Key Distribution Center and get temporary keys to access locations on the network. Microsoft introduced their version of Kerberos in Windows2000. Each user and service on the network is a principal.
It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. Connecting to an Oracle Database Server Authenticated by Kerberos After Kerberos is configured you can connect to an Oracle database server without using a user name or password. In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication.
The benefits gained by using Kerberos for domain-based authentication are. It might also use NTLM which is also a provider in windows authentication. In our example the Nginx server IP address is 1921681511.
It is required that Negotiate comes first in the list of providers. Kerberos authentication must be enabled in Active Directory. The idea behind Kerberos is to authenticate users while preventing passwords from being sent over the internet.
It should already be enabled as the default. A free implementation of this protocol is available from the Massachusetts Institute of Technology. Services that run on Windows operating systems can impersonate a client computer when.
Kerberos authentication protects user credentials from hackers. Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. Authentication is mutual so client and server authenticate at the same steps and they are both sure they are.
This protocol keeps passwords away from insecure networks at all times even during user verification. In this episode of Lightboard Lessons Jason covers the basics of the Kerberos authentication protocol. In this scenario clients must present Kerberos tickets for authentication.

Data Factory Is Now A Trusted Service In Azure Storage And Azure Key Vault Firewall Reading Data Azure Data
Source Image @ www.pinterest.com

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide
Source Image @ www.pinterest.com

Kerberos Architecture Computer Help Windows Server Microsoft
Source Image @ www.pinterest.com
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography
Source Image @ www.pinterest.com

Kerberos Architecture Computer Help Windows Server Microsoft
Source Image @ www.pinterest.com
If the posting of this website is beneficial to our suport by posting article posts of the site to social media marketing accounts that you have such as for example Facebook, Instagram among others or may also bookmark this blog page with all the title Kerberos Architecture Computer Help Windows Server Microsoft Work with Ctrl + D for laptop devices with House windows operating-system or Command word + D for personal computer devices with operating system from Apple. If you use a smartphone, you can even use the drawer menu of the browser you use. Whether its a Windows, Mac pc, iOs or Android operating-system, you'll still be able to download images utilizing the download button.
