Kerberos ~ Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials. Κέρβερος latinisiert Cerberus dt. Indeed recently has been searched by consumers around us, maybe one of you personally. People now are accustomed to using the internet in gadgets to view image and video data for inspiration, and according to the title of this post I will talk about about Kerberos Kerberos Double Hop is a term used to describe our method of maintaining the clients Kerberos authentication credentials over two or more connections.
If you re searching for Kerberos you've come to the ideal place. We have 6 images about kerberos including images, photos, pictures, backgrounds, and more. In these page, we also provide number of graphics available. Such as png, jpg, animated gifs, pic art, symbol, blackandwhite, transparent, etc.

Kerberos Security Apache Spark Spark Apache
Source Image @ www.pinterest.com
I princip går det ut på att användaren identifierar sig hos den tredje parten kerberosservern med sitt namn och sitt lösenord känt endast för kerberosservern och användaren.

Kerberos. Kerberos may refer to. 1 Det finns olika versioner om Kerberos svans enligt vissa var den en draksvans och enligt andra en orm. In Kerberos Authentication server and database is used for client authentication.
Kerberos MC Kankaanpää chapter Kankaanpää. Kerberos is a network authentication protocol. 689 tykkäystä 1 puhuu tästä 79 oli täällä.
Kerberos Vault is installed in a Kubernetes cluster and for every additional cluster you are setting up Kerberos Vault you will need an additional license. Remove this registry value when it is no longer needed so that performance is not degraded on the computer. Kerberos protokół uwierzytelniania i autoryzacji w sieci komputerowej z zastosowaniem centrum dystrybucji kluczy zaprojektowany w Massachusetts Institute of Technology MIT.
You might want to. Kerberos runs as a third-party trusted server. Kerberos protocol a computer network authentication protocol to allow server communication over a non-secure network.
It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. The reason why you might need additional Kerberos Vaults is because of edge processing. Kerberos Dante a character from Saint Seiya.
Kerberos ist ein verteilter Authentifizierungsdienst Netzwerkprotokoll für offene und unsichere Computernetze wie zum Beispiel das Internet der von Steve Miller und Clifford Neuman basierend auf dem Needham-Schroeder-Protokoll zur Authentifizierung 1978 entwickelt wurde. Die zurzeit aktuelle Version ist Kerberos 5. Please make sure you read the previous Kerberos for the busy admin.
Enable Kerberos event logging on a specific computer. Kerberos mythology or Cerberus the hound of Hades. A free implementation of this protocol is available from the Massachusetts Institute of Technology.
Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. Kerberos var avkomma till Tyfon och Echidna. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet.
Hes a big 3 headed dog with a snake for a tail and a really bad temper. The protocol was named after the character Kerberos or Cerberus from Greek mythology the ferocious three-headed guard dog of Hades. Kerberos moon a moon of Pluto.
According to myth Kerberos you might know him as Cerberus guards the Gates to the Underworld. Kerberos Authentication Explained. If the Parameters subkey does not exist create it.
Kerberos Turvallisuuspalvelut on Poliisihallituksen hyväksymä vartioimisliike sekä järjestyksenvalvoja- voimankäyttö- ja ampuma-asekouluttaja. Yrityksen toimipisteet sijaitsevat Lappeenrannassa Kotkassa Kuopiossa Tampereella Turussa Helsingissä ja Oulussa mutta suoritamme toimeksiantoja koko Suomessa sekä ulkomailla. Kerberos is available in many commercial products as well.
Kérberos latin Cerberus är i grekisk mytologi den trehövdade hund som vaktar ingången till dödsriket där Hades regerar. Kerberos bygger på en betrodd tredje part i kommunikationen mellan användaren och tjänsten. Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services.
Kerberos ˈ k ɜːr b ər ɒ s is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Kerberost kujutati paljudes antiik-kreeka ja antiik-rooma kirjandusteostes samuti nii antiik- kui ka moodsas kunstis ja arhitektuuris. Kerberos Productions a game development studio.
1 När de dödas själar närmar sig dödsriket spänner Kerberos sina kedjor och blottar sina tänder för. In this fashion we can retain the users credentials and act on behalf of the user in further connections to other servers. It uses secret-key cryptography and a trusted third party for authenticating client.
In the modern world MIT Computer Scientists used the name and visual of Kerberos for their computer network authentication protocol. Powstało też wiele interfejsów programistycznych pozwalających wbudowywać mechanizmy bezpieczeństwa dostarczane przez serwer Kerberos do aplikacjiJednym z nich jest interfejs w języku Java nazwany General. Auch Zerberus Dämon der Grube ist in der griechischen Mythologie ein zumeist mehrköpfiger Höllenhund der den Eingang zur Unterwelt bewacht damit kein Lebender eindringt und kein Toter herauskommt.
Kerberos vanakreeka keeles Κέρβερος ladina keeles Cerberus on vanakreeka ja vanarooma mütoloogias esinev mitmepealine koer kes valvab Allilma väravaid et hoida põgenemast neid kes on ületanud Styxi jõe. Sie ist in RFC 4120 definiert und nutzt ASN1 zur Codierung.

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base
Source Image @ www.pinterest.com

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain
Source Image @ www.pinterest.com
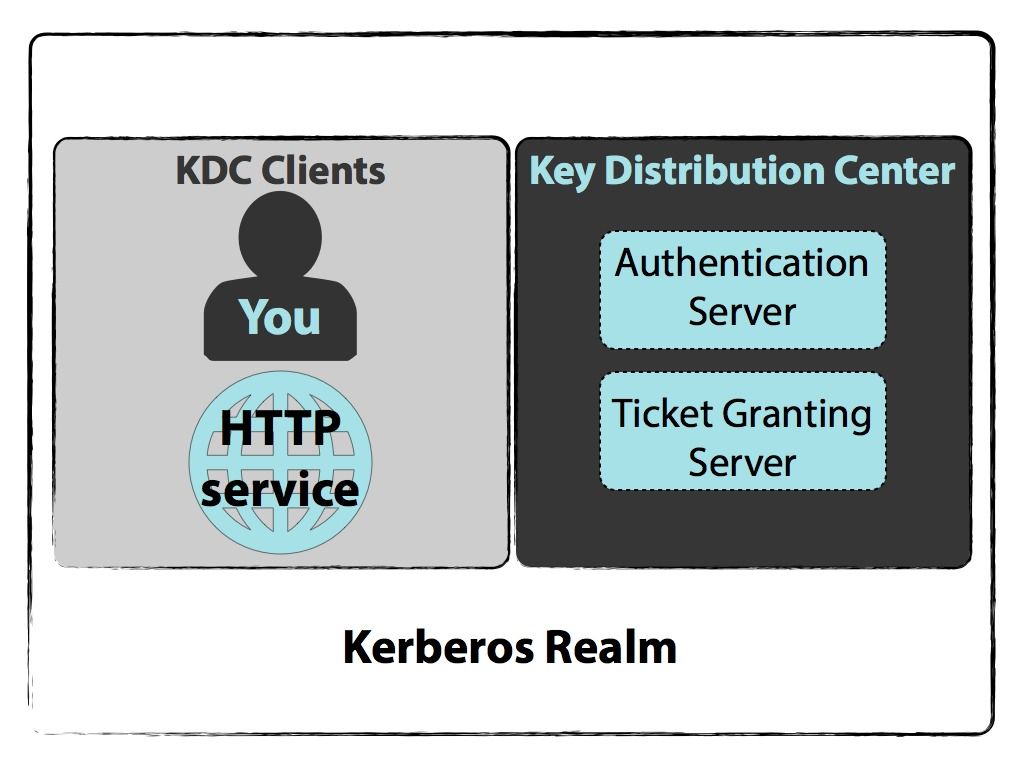
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography
Source Image @ www.pinterest.com

Kerberos Web Graphic Design Vintage Graphic Design Poster Design
Source Image @ www.pinterest.com

Pin On Storage
Source Image @ www.pinterest.com
If the posting of this site is beneficial to our suport by sharing article posts of this site to social media marketing accounts that you have such as Facebook, Instagram among others or may also bookmark this blog page using the title Pin On Storage Employ Ctrl + D for computer system devices with Home windows operating-system or Command + D for pc devices with operating system from Apple. If you use a smartphone, you can also utilize the drawer menu of the browser you utilize. Whether its a Windows, Macintosh personal computer, iOs or Android os operating-system, you'll still be in a position to download images utilizing the download button.
